Introduction
In the new paradigm of the connected world, where everything and everyone has access to the Internet, having a totally secure network is difficult to imagine. Today we see how digitization is advancing rapidly, within education, health and government, offering more and more services and simplifying access to data and procedures, generating a high stress to cybersecurity teams. This coupled with the geopolitical climate we are living, see the latest attacks on administrations that we have suffered here in Spain, does not allow us to be distracted or even take a break and forces us to be continuously updating policies and technology at the security level.
Source of threats – Zero Trust model becomes a must
We have always had the concept of perimeter in the network, where the bad guys were outside and the data and assets to protect were inside. Today that perimeter is fading when we have employees working remotely, equipment that is not updated, IoT devices connected in anywhere locations, proliferation of remote offices… they only make things easier for attackers, who will try to compromise an internal device, steal a credential, look for lateral movements and take advantage of lax access policies.
The already well known Zero Trust model tries to respond and update our cybersecurity strategy, under this new framework we will not trust anyone inside nor outside the network, as it forces us to restrict access as much as possible and the level of trust is treated as another vulnerability.
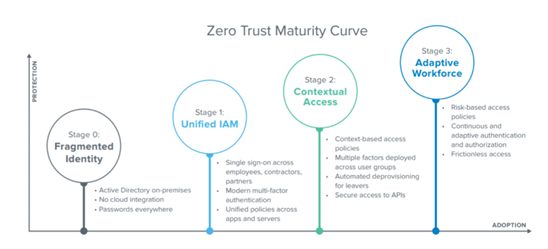
From that point on, we can work with the available technologies, to adapt the level of maturity, in the different stages of Zero Trust, where we start from fragmented identities, without integration in the cloud and on-premises directories, we must evolve to SSO systems for all users who use the services, in addition to applying two-factor authentication on all accesses, and also have a unified access control policy.
In the later stages, context-based access, where identity takes a second level, and the posture of the device together with the location, will be the focus of the access policy. An adaptive process with continuous access authorization, and not just at the beginning, allows us to have risk-based policies.
How security services unify and simplify operations
The simple application of security and deployment from a unified portal will help us to quickly put into context the security controls to be applied. Having security services in the cloud, which drastically reduce operations and give us flexibility when deploying access or remote sites, will help us to optimize internal processes.
To this we add the fact that, from a central point in a simple way, we should be able to apply control policies based on source and identity, along with other security features that we may need. Technologies such as IPS/IDS, SSL traffic decryption, user identification, Secure web Gateway, DLP or Sandboxing, applied from a central point in a unified access in the cloud, can offer us a quick control with the security policies that our organization needs.
Another key is to be able to count on network monitoring and analysis technologies, where we will be able to discover inappropriate access, in addition to analyzing the behavior of users and devices. Technologies such as NTAs – Network Traffic Analysis can help us to discover threats in the network, understanding the traffic behavior, along with bad access configurations in the network devices, which can compromise security by offering more access than necessary.
Conclusion
With these security services in the cloud, the entire operation is simplified, and we no longer have security devices distributed throughout the network, which have to be continuously updated and configured. In addition we can move the costs from a CAPEX model to OPEX, which gives us a zero cost of ownership. The operational savings are also clear, as it allows any user without deep technical knowledge in security, to deploy a new access immediately, have a fast and unlimited scaling if necessary and take advantage of platform updates with new features and improvements without having to do anything. Having integrated network monitoring tools will help us to better understand our traffic and discover threats and inappropriate access.
Being able to apply all these policies in a unified way from a central point will help us to comply with the Zero Trust framework and improve our security and operations substantially.
Teldat, a leading vendor in the sector, applies its be.Safe XDR tool, which is capable of monitoring the network, and also with its be.Safe Premium service that allows advanced security policies to be applied to remote users and headquarters. Offering the capacity to allow or disallow connections based on the reputation of the accessed site, analyzing traffic in depth and stopping any threat before it can reach the users.